ComPass
ComPass: Proximity Aware Common Passphrase Agreement Protocol for Wi-Fi devices Using Physical Layer Security
K. Reaz, A. Pinz, G. Wunder
Problem Statement
Connectivity is the key to the world of business, entertainment, education or government services. Undoubtedly, wireless medium is the last mile of this communication pipeline. While cellular dominates the mobility scenario, 802.11 a.k.a Wi-Fi is the single most widely used technology to access the internet when it comes to streaming movies on the smart TV at home, securing premises with IP cameras, or merely sharing vacation photos from a hotel room or cafe.
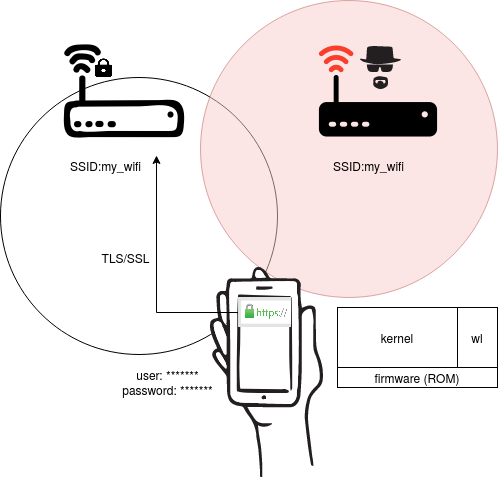
How would you connect devices lacking proper input methods to your Wi-Fi network? You then simply confirm with a push-button, comparing alphanumeric strings, scanning QR code or blindly accept them to your network. Existing standards rely on public key cryptography or on a secondary medium to allow secure joining. First one needs a very large key-size (at least 4200 bits) and may soon become a victim to quantum computers’ cracking capability, and the latter does not scale well.
ComPass
- ComPass protocol forgoes the necessity of creating a fixed Wi-Fi "passphrase", and the dependency on PublicKey (in WPA3). While it is convenient, a user might choose weak "passphrase" or in the worst case keep using the factory default one.
- With the new protocol it is possible to create unique passphrase for each devices and can be refreshed automatically or on demand. Now the head-less IoT devices can agree on a common passphrase based key without needing user input or poor static pre-installed key.
- ComPass is designed such a way that the passphrase agreement protocol only works when both devices are within closed proximity. This is especially useful for ensuring that the legitimate user is indeed within the perimeter such as Café and not for someone who is across the street even though Wi-Fi signal is available.
- It is the first of its kind to derive passphrase from phase information using PLS methods making the passphrase strong, robust and with increased security.
- We implemented ComPass on commercial off-the-shelf (COTS) hardware. The implementation is open-source and available to try out from our git repository to compile and flash compatible Wi-Fi device.
How does it work?
Let us define entities of the ComPass protocol. Access Point is kept hidden (to reduce Evil twin attacks) and it has an Authenticator with rich user interface. Enrollee is a device with limited interface (can have rich user interface too). Before initiating the protocol devices are brought within close proximity (less than 3m ). Summary of the protocol steps are as follows:
1) With a button (simple power button or existing WPS button can be re-programmed for this purpose) press or after booting Enrollee broadcasts its name/id with random nonce by turning itself into a temporary access point.
(2) Authenticator verifies and confirms the Enrollee from an app or Wi-Fi settings
a. Authenticator and Enrollee performs procedures mentioned in A-D and generate common passphrase1. Once connected, Authenticator sends (SSID + APMAC) to Enrollee. Subsequently, it sends Enrollee’s MAC+ passphrase1 to Access Point. This is already encrypted since the Authenticator joined the network beforehand.
b. Enrollee switch to Wi-Fi Client mode after receiving (SSID + AP-MAC) from Authenticator. It sends Association request to Access Point appending hashed passphrase1
c. Access Point verifies the request by comparing hashed passphrase1. If successful, it initiates procedures mentioned in A-D
(3) Access Point and Enrollee generates passphrase2 performing procedures mentioned in A-D
(4) If successful, Access Point allows Enrollee to connect and it notifies Authenticator, else Enrollee returns to step (2)b. Finally, Authenticator and Access Point deletes the passphrase1